
ToddyCat APT evolves to target Outlook archives and Microsoft 365 tokens
Attackers behind the ToddyCat advanced persistent threat (APT) toolkit have adapted to stealing Outlook mail data […]

Alliances between ransomware groups tied to recent surge in cybercrime
A seasonal surge in malicious activity combined with alliances between ransomware groups led to a 41% […]

Agentic AI – die besten Security-Anwendungsfälle
srcset=”https://b2b-contenthub.com/wp-content/uploads/2025/10/DC-Studio_shutterstock_2626368691_16z9.jpg?quality=50&strip=all 5058w, https://b2b-contenthub.com/wp-content/uploads/2025/10/DC-Studio_shutterstock_2626368691_16z9.jpg?resize=300%2C168&quality=50&strip=all 300w, https://b2b-contenthub.com/wp-content/uploads/2025/10/DC-Studio_shutterstock_2626368691_16z9.jpg?resize=768%2C432&quality=50&strip=all 768w, https://b2b-contenthub.com/wp-content/uploads/2025/10/DC-Studio_shutterstock_2626368691_16z9.jpg?resize=1024%2C576&quality=50&strip=all 1024w, https://b2b-contenthub.com/wp-content/uploads/2025/10/DC-Studio_shutterstock_2626368691_16z9.jpg?resize=1536%2C864&quality=50&strip=all 1536w, https://b2b-contenthub.com/wp-content/uploads/2025/10/DC-Studio_shutterstock_2626368691_16z9.jpg?resize=2048%2C1152&quality=50&strip=all 2048w, https://b2b-contenthub.com/wp-content/uploads/2025/10/DC-Studio_shutterstock_2626368691_16z9.jpg?resize=1240%2C697&quality=50&strip=all 1240w, https://b2b-contenthub.com/wp-content/uploads/2025/10/DC-Studio_shutterstock_2626368691_16z9.jpg?resize=150%2C84&quality=50&strip=all 150w, […]
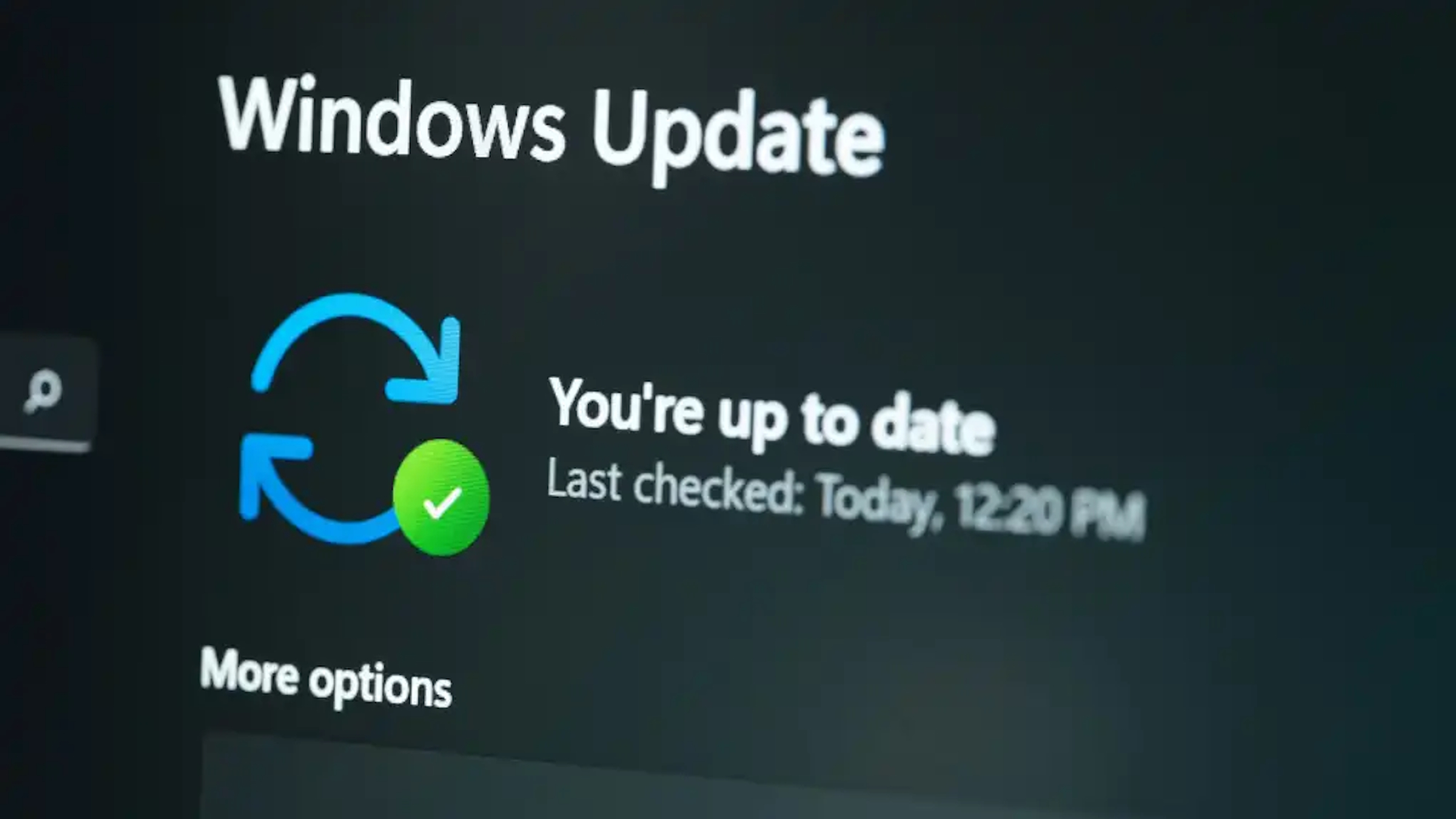
New ClickFix attacks use fake Windows Update screens to fool employees
CSOs and Windows admins should disable the ability of personal computers to automatically run commands to […]

Developers left large cache of credentials exposed on code generation websites
A large trove of sensitive credentials, authentication keys, configuration data, tokens, and API keys has been […]

Telecom security reboot: Why zero trust is the only way forward
Telecom networks are everywhere. They keep the world moving — all the way from managing data, […]

Fluent Bit vulnerabilities could enable full cloud takeover
Fluent Bit, a widely deployed log-processing tool used in containers, Kubernetes DaemonSets, and major cloud platforms, […]

Hackerangriff auf Hochschule Mainz
Die Hochschule Mainz wurde gehackt. Hochschule Mainz Die Hochschule Mainz ist nach eigener Einschätzung am Montag […]

7 signs your cybersecurity framework needs rebuilding
Cybersecurity frameworks are the guidelines enterprises use to guard against cyberattacks. The typical framework describes the […]
Quantum Computing Risks: What CISOs Must Prepare for Before 2026
There is an unprecedented transformation in the enterprise security environment. Quantum computing that used to be […]
